To Share is to Show You Care!
Cryptocurrency has revolutionized the financial landscape, providing individuals with unprecedented control over their funds. However, this autonomy comes with its own set of challenges, particularly when it comes to safeguarding private keys. Losing access to your private keys can mean losing access to your funds permanently. In this blog post, we’ll explore the risks associated with forgotten private keys and unveil a robust solution to ensure the safety of your crypto assets.
1. Key Risks of Forgotten Private Keys
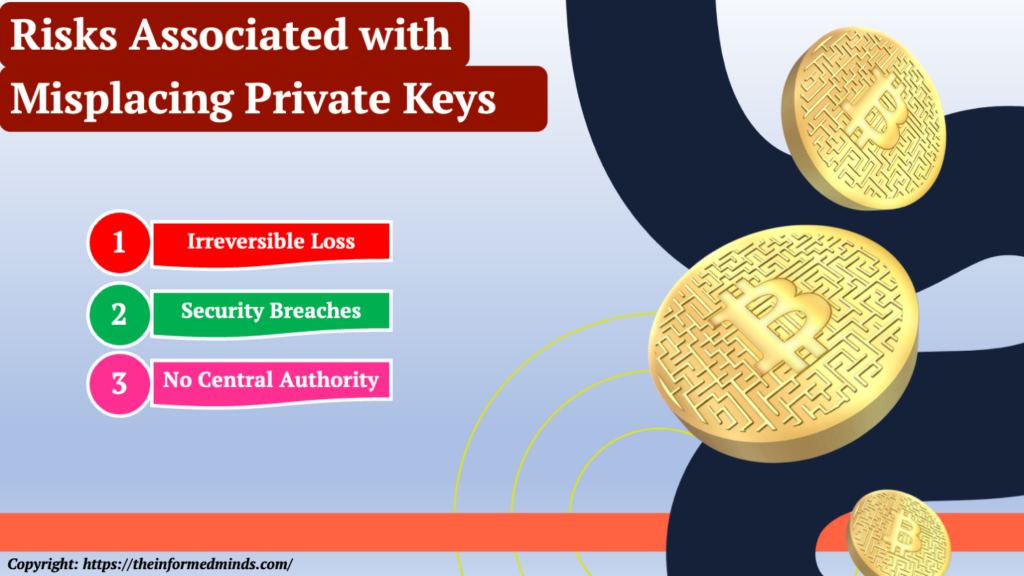
1.1 Irreversible Loss
When users lose access to their private keys, they essentially lose control over their cryptocurrency holdings permanently. Unlike traditional banking systems, where password recovery or account retrieval options exist, cryptocurrencies are decentralized and offer no centralized authority to assist in key recovery.
1.2 Security Breaches
Storing private keys on vulnerable devices or platforms exposes them to potential security breaches. If a hacker gains access to these keys, they can easily transfer funds out of the associated wallets, leading to significant financial losses for the owner.
1.3 No Central Authority
Cryptocurrencies operate on decentralized networks, meaning there’s no central authority to turn to for key recovery or transaction reversal. Once private keys are lost, there is no fallback mechanism, making it crucial for users to take proactive measures to protect and secure their keys.
2. The Solution: Crypto Vault – Your Key to Unshakeable Security
Crypto Vault is a comprehensive solution designed to address the challenges associated with forgotten private keys and enhance the security of cryptocurrency holdings. It provides users with a robust and reliable platform to safeguard their assets through innovative features and security measures.
3. Key Features of Crypto Vault
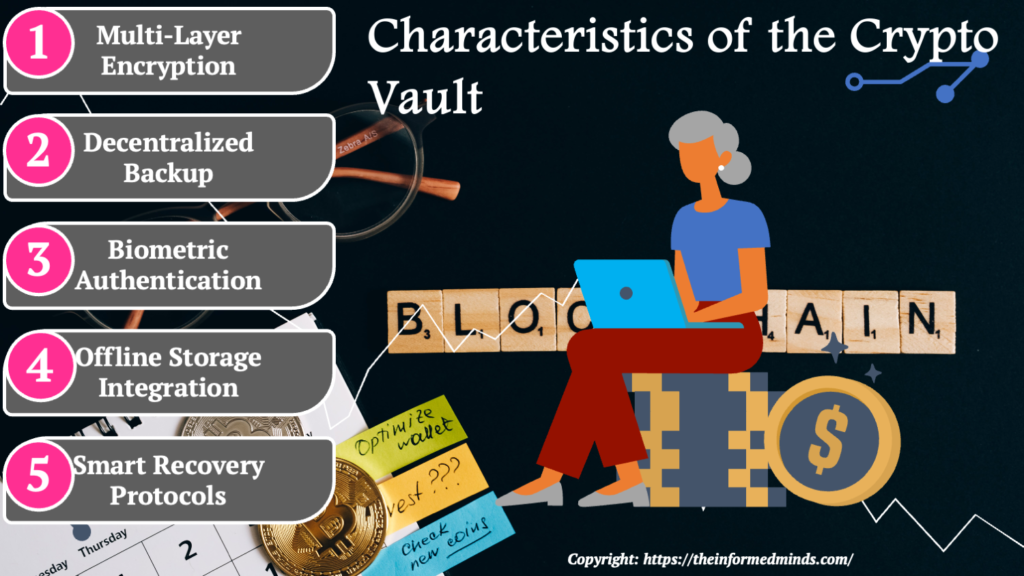
3.1 Multi-Layer Encryption
Crypto Vault employs advanced encryption algorithms to create multiple layers of security. This ensures that private keys are well-protected against any attempts at unauthorized access or hacking.
3.2 Decentralized Backup
To eliminate the risk of a single point of failure, Crypto Vault decentralizes the backup process. Private keys are fragmented and distributed across various secure locations, reducing the likelihood of complete key loss.
3.3 Biometric Authentication
Enhancing user authentication, Crypto Vault incorporates biometric data. Only users with the unique biometric information tied to the account can access private keys and authorize transactions, adding an extra layer of security.
3.4 Offline Storage Integration
Recognizing the vulnerabilities associated with online storage, Crypto Vault seamlessly integrates with hardware wallets and secure cold storage solutions. This offline storage option provides an additional layer of protection against online threats.
3.5 Smart Recovery Protocols
In the event of key loss, Crypto Vault offers smart recovery protocols. Users can follow a secure and streamlined process to regain access to their funds by utilizing the decentralized fragments of their private keys.
4. How Crypto Vault Works
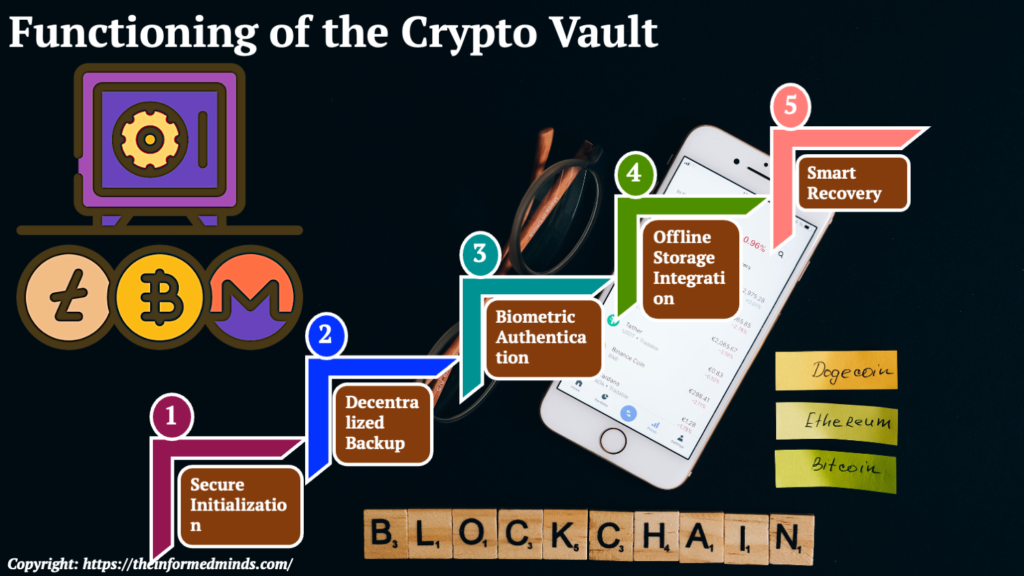
Step 1: Secure Initialization
Users initiate the process by creating a Crypto Vault account. During this setup, they provide biometric data and configure personalized security settings to establish a secure foundation.
Step 2: Decentralized Backup
Crypto Vault splits and encrypts private keys, creating fragments that are then distributed across multiple secure locations. This decentralized backup reduces the risk of complete key loss.
Step 3: Biometric Authentication
Access to private keys and the authorization of transactions are tied to biometric authentication. Only users with the correct biometric data can interact with their crypto assets.
Step 4: Offline Storage Integration
To enhance security further, Crypto Vault allows users to integrate with hardware wallets or secure cold storage devices, ensuring that private keys are stored in an offline environment.
Step 5: Smart Recovery
In the unfortunate event of key loss, users can initiate the smart recovery process. This involves using the decentralized fragments of their private keys to regain access to their funds, ensuring a secure and reliable recovery mechanism.
Conclusion
Crypto Vault stands as a formidable solution to the risks associated with forgotten private keys, offering unparalleled security and peace of mind. By implementing multi-layered encryption, decentralized backups, biometric authentication, and smart recovery protocols, Crypto Vault ensures that your cryptocurrency investments remain in safe hands, even in the face of unexpected challenges. Embrace the future of crypto security with Crypto Vault and safeguard your financial freedom.
Frequently Asked Questions
Q1: What happens if you lose your private key to your cryptocurrency?
A: If you lose your private key to your cryptocurrency, you lose access to your funds permanently. Private keys are the cryptographic keys that provide control over your digital assets. Without the private key, you cannot access, transfer, or recover your cryptocurrency holdings.
Q2: Why is a crypto private key important?
A: A crypto private key is crucial because it is the secret code that allows individuals to access and control their cryptocurrency holdings. It serves as a digital signature, enabling the owner to initiate transactions, transfer funds, and prove ownership of the associated assets on the blockchain.
Q3: What if you lose your hardware wallet?
A: Losing a hardware wallet, while not resulting in the loss of funds directly, can be risky. If you have a backup of the recovery seed, you can restore your wallet on another device. However, if the hardware wallet and recovery seed are both lost, the funds are at risk of being inaccessible, emphasizing the importance of securely storing recovery information.
Q4: Can crypto private keys be hacked?
A: While crypto private keys themselves are not “hacked” in the traditional sense, they can be compromised through security breaches, phishing attacks, or malware. Ensuring secure practices, such as using reputable wallets, employing hardware wallets, and avoiding suspicious links, helps mitigate the risk of private key compromise.
Q5: What happens if you lose your private key?
A: If you lose your private key, you lose access to your cryptocurrency holdings. Private keys are essential for signing transactions and proving ownership. Recovery options are limited, emphasizing the need for secure storage and backup mechanisms to prevent irreversible loss.
Q6: What happens to lost Bitcoin wallets?
A: Lost Bitcoin wallets, usually resulting from lost private keys or forgotten passwords, lead to the permanent inaccessibility of the associated funds. Since Bitcoin operates on a decentralized network, there is no central authority to recover lost wallets, underscoring the importance of secure key management.
Q7: Why is a private key needed?
A: A private key is needed to prove ownership and control over cryptocurrency assets. It serves as a unique identifier, enabling users to sign transactions and access their funds on the blockchain. Without a private key, users cannot engage in cryptocurrency transactions.
Q8: How do I protect my private key crypto?
A: To protect your crypto private key, consider:
- Using hardware wallets for secure offline storage.
- Implementing multi-factor authentication.
- Regularly updating and securing devices used for crypto transactions.
- Avoiding sharing private keys or recovery seeds.
- Keeping backups in secure, offline locations.
Q9: How do you brute force a Bitcoin private key?
A: Brute forcing a Bitcoin private key involves attempting all possible combinations until the correct key is found. However, due to the astronomical number of possible combinations, it is practically impossible to brute force a Bitcoin private key within a reasonable timeframe, making this method unfeasible.
Q10: What happens if a crypto wallet goes out of business?
A: If a crypto wallet provider goes out of business, users may face challenges accessing their funds. It highlights the importance of using wallets with open-source code or ensuring the ability to export private keys. Users should stay informed about wallet providers’ status and migrate funds if necessary.
Q11: Can someone hack my hardware wallet?
A: While hardware wallets are generally secure, no system is entirely hack-proof. However, the offline nature of hardware wallets makes them less susceptible to online attacks. Users should follow best practices, such as keeping the device updated, setting a strong PIN, and ensuring the recovery seed is securely stored.
Q12: Can crypto be stolen from a hardware wallet?
A: Cryptocurrency stored in a hardware wallet is considered highly secure. However, if someone gains access to your recovery seed or PIN, they could potentially steal your crypto. It is crucial to keep recovery information secure and avoid sharing it with anyone.
Q13: Can a private key be stolen?
A: Yes, private keys can be stolen through various means, including hacking, phishing, or physical theft. Users must take proactive measures to secure their private keys, such as using hardware wallets, employing secure storage methods, and being cautious of online threats.
Q14: How do hackers get your private key?
A: Hackers can obtain private keys through phishing attacks, malware, social engineering, or exploiting vulnerabilities in software. It underscores the importance of cybersecurity measures, such as using reputable wallets, avoiding suspicious links, and keeping devices secure.
Q15: Is a private key really safe?
A: The safety of a private key depends on the security measures taken by the owner. While private keys themselves are cryptographically secure, user practices, such as secure storage, regular updates, and cautious online behavior, significantly contribute to the overall safety of private keys.
The Informed Minds
I'm Vijay Kumar, a consultant with 20+ years of experience specializing in Home, Lifestyle, and Technology. From DIY and Home Improvement to Interior Design and Personal Finance, I've worked with diverse clients, offering tailored solutions to their needs. Through this blog, I share my expertise, providing valuable insights and practical advice for free. Together, let's make our homes better and embrace the latest in lifestyle and technology for a brighter future.